Network simulator 12.0 Software - Man In The Middle - ARP Spoofing
 Download the network diagram used
Download the network diagram used
A Man In The Middle (MITM) attack can occur in different ways. The one proposed is based on ARP Spoofing, an exploitation of a weakness in the ARP protocol. The Man In The Middle attack can lead to denial of service (if the packets are blocked by the hacker), or the consultation/modification of data passing through the hacker.
The simulator takes these two possibilities.
This network diagram is used to demonstrate all attacks. The hacker will use the Hacker or MITM positions :
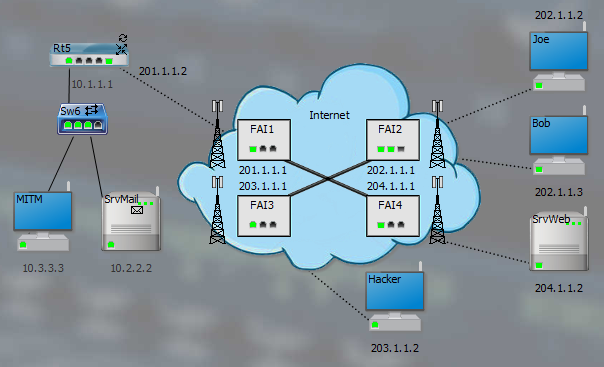
1. Build the attack
To define an attack, click on the Failures button (Build group). Right click on MITM and choose Define attack or double-click :

Choose MITM (ARP Spoofing) as the objective. Check Retransmit captured packets to go unnoticed. By focusing on the target IP address, click on the Rt5 and SrvMail cards connected to Sw6 (same IP network as MITM). Activate attack :

2. Launch the attack
The attack is ready to be launched (manually or automatically). Validate/close the windows and choose a simulation speed with breakdowns and attacks. The hacker icon appears on the station :

In the context menu of MITM, choose Launch attack (MITM via ARP Spoofing) :

To check the effect of the attack, send an IP packet from SrvMail to Rt5 for example, but a ping or a mail poll from Joe would also do :

Observe for the packet the message modified by MITM (for other protocols, the packet is not modified).
Also observe that the simulation does not stop after sending the packet, because the Mac-IP tables are initialized at the start of the simulation. This allows therefore attempt other transfers with the attack active. Here is the Mac-IP table of SrvMail before the attack :
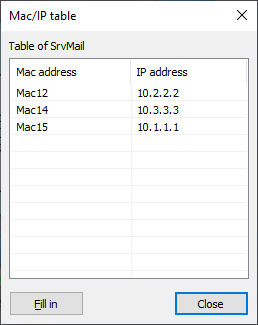
Then after the attack (traffic directed to Mac14) :

To combat this attack, we can define static Mac-IP tables, which are unlikely to be possible on a large scale. More suitable, switches offer generally protection against ARP Spoofing : An ARP response without a corresponding ARP request first is deleted. The context menu of the switch offers the option :

Demonstration of how it works by relaunching the attack :
